Tag: firewalls
RHCE Exam Objective: Use Firewalld
by jfargen on Nov.06, 2016, under Cert, RHCE, Training
Just going to cover the basics, for reference refer to manpage.
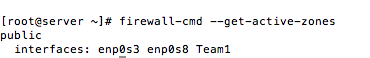
Check what the current active zones:
# firewall-cmd –get-active-zones
Check the config of a zone
# firewall-cmd –info-zone=public
Open a port for a service in an active zone. Note that this is temporary. A reload or reboot of the firewall will blow this config away.
# firewall-cmd –zone=public –add-service=http
Close a port for a service in an active zone. Note that this too is temporary.
# firewall-cmd –zone=public –remove-service=http
To make this change active and permanent the command needs to be run twice, once with –permanent in place.
# firewall-cmd –permanent –zone=public –add-service=http
# firewall-cmd –zone=public –add-service=http
Now view the info for the zone and notice how the http service has been added.
Configuring a host to work as a NAT gateway
To enable NAT you first need to configure the kernel to forward IPv4 traffic. This can be done by adding the following file to
/etc/sysctl.d/98-ipv4-forward.conf with the following contents.
# cat /etc/sysctl.d/98-ipv4-forward.conf
net.ipv4.ip_forward = 1
To immediately enable this setting then run the following command.
# sysctl -w net.ipv4.ip_forward=1
Next add your interfaces to different zones and reload the firewalld config.
# firewall-cmd –zone=external –add-interface=enp0s3 –permanent
# firewall-cmd –zone=internal –add-interface=Team1 –permanent
# firewall-cmd –complete-reload
Next enable masquarading on your external interface.
# firewall-cmd –zone=external –add-masquerade –permanent
Then add a postrouting rule using rich iptables rules.
# firewall-cmd –permanent –direct –passthrough ipv4 -t nat -I POSTROUTING -o enp0s3 -j MASQUERADE -s 10.0.0.0/24
There use to be an issue where after a restart the adapter would lose its zone config because it was not added into the ifcfg- file. This seems to no longer be the case in RHEL7.3, but it is something to watch for on the RHCE exam if it is an older version.
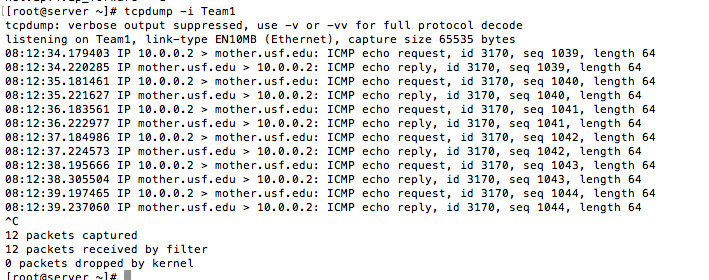
As a test I pinged an ip address on the internet from the client VM and ran tcpdump on the server VM. As you can see the ICMP traffic is traversing through the server VM as expected.
For more information on the configuring RHEL7 as a NAT Gateway check out this blog.