Tag: linux
RHCE 7 Exam Objective: Configure IPv6
by jfargen on Nov.06, 2016, under Cert, RHCE, Training
Configure IPv6
This was a little painful, it maybe an issue with VBox, teaming, or IPv6. I expect in the EX300 exam simply adding the IPV6ADDR=wxyz.wxyz… and nmcli con reload will work with out any issues. To get this working on my VBox setup took a lot more work and research.
First, here is the configuration of the NAT network.
Next, there was an issue with duplicate local IPv6 addresses. First, I disabled IPv6 on the enp0s8 and enp0s9, then I disabled dad, on both the server and client VMs.
Here are the relevent sections in /etc/sysconfig/network-scrtips/ifcfg-enp0s[8-9]
IPV6INIT=no
IPV6_AUTOCONF=no
IPV6_DEFROUTE=no
IPV6_PEERDNS=no
IPV6_PEERROUTES=no
IPV6_FAILURE_FATAL=no
Then I added this file and contents to disable dad:
# cat /etc/sysctl.d/90-ipv6-disable-dad.conf
net.ipv6.conf.default.optimistic_dad=1
net.ipv6.conf.default.accept_dad=0
net.ipv6.conf.enp0s8.optimistic_dad=1
net.ipv6.conf.enp0s8.accept_dad=0
net.ipv6.conf.enp0s9.optimistic_dad=1
net.ipv6.conf.enp0s9.accept_dad=0
net.ipv6.conf.Team1.optimistic_dad=1
net.ipv6.conf.Team1.accept_dad=0
net.ipv6.conf.all.use_tempaddr=-1
Then I went to this site to generate a local Unique Local Address (ULA):
You can just pick the first subnet.
My subnet was fdf8:d910:d680::/64.
I used fdf8:d910:d680::0001/64 server VM IPv6 address and fdf8:d910:d680::0002/64 for the client VM Ipv6 address.
Example: Add this line to /etc/sysconfig/network-scripts/ifcfg-Team1 on the server VM
IPV6ADDR=fdf8:d910:d680::0001/64
Then start the VMs once this is completed.
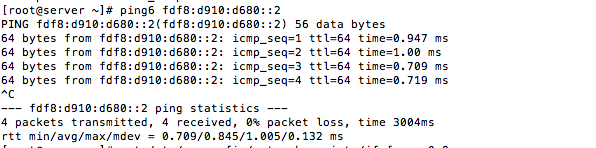
To test, I tried pinging the client VM from itself, which was successful.
Then I attempted to ping the client VM from the server VM which was also successful.
If you want my info on IPv6 their are excellent tutorials at the site TunnelBroker. They also have an interesting service that allows you to tunnel IPv6 over IPv4, but the last time I checked they had a feud with Cogent Communications that broke half the IPv6 internet.
Red Hat Certified Systems Administrator (RHCSA): Passed
by jfargen on Apr.11, 2014, under Uncategorized
Today I took the RHCSA exam, here in Tampa, FL. Mostly barred from commenting on the exam, but it wasn’t to straining. Though I definitely made some mistakes.
Here is a link to verify my results.
How to get a hard drive serial number from udev.
by jfargen on Dec.26, 2012, under Uncategorized
Some times a hard drive will fail in such a way that tools like smartctl or hdparm is unable to get the hard drive serial number or in certain circumstances will give the wrong hard drive serial.
This may work some of the time, but it won’t always work depending on the type of failure a drive is experiencing. It is definitely a better alternative to try rather than getting someone to go down to the data center and pulling your drive.
*Note that WordPress does something to the hyphens and when rendered on the webpage it is a different character. When entering the command ensure that you enter (hyphen)(hyphen) before each option passed in the command.
$ /sbin/udevadm info –query=property –name=drive| grep -i serial
Just replace drive for which physical drive you are trying to get details. In my case I use the command like so as an example.
$/sbin/udevadm info –query=property –name=sda| grep -i serial
KVM:Reset Linux Guest Password and/or Password Expiration
by jfargen on Dec.21, 2012, under Work and stuff
The post is from the stand point of RHEL hypervisor with a KVM CentOS Linux guest using a raw image file as a backing store and the openssl package, but it could easily be applied to different distros, backing stores, or even booting a Linux livecd as long as you can get the necessary packages. Some steps may vary depending on what kind of backing store you are using for the image and the partitions your OS is installed. This process could also be used to do many other things like increasing the time for password expirations.
First mount the image as a loopback device:
$ sudo losetup /dev/loop0 /var/lib/libvirt/images/virtcort011ccxra.img # note that is a zero at the end of /dev/loop
Next add the partition mappings:
$ sudo kpartx -av /dev/loop0
In my CentOS installation I was using LVM and the next few steps are LVM specific:
Use vgscan to find the LVM volume
$ sudo vgscan
This located the new LVM volume group VolGroup00 # again note that is zero zer at the end of VolGroup. You will use this group in the next step.
Activate LVM Volume Group:
$ sudo vgchange -ay VolGroup00
You can use lvs to find the Volume where your / (root) file system is mounted:
$ sudo lvs
Next mount the volume:
$ sudo mount /dev/VolGroup00/LogVol00 /mnt/linuxrescue
You should be able to see directories in the volume:
$ ls /mnt/linuxrescue
Now generate the new password for the guest:
$ openssl passwd -1 -salt ranNum # for the salt substitute random numbers and letters for ranNum.
Password:
$1$ranNum$N6s5hhYltlYQPnMDdxYy1 # you can see your salt + hash
Now copy this string into /etc/shadow:
$ sudo vi /mnt/linuxrescue/etc/shadow
In editing your shadow file you will see something like below your salt+hash should be substituted as below for the user password you would like to reset.
root:$1$ranNum$N6s5hhYltlYQPnMDdxYy1:15492:1:90:7:::
If you want to change the length of time for password expirations the next step will show you how.
$ sudo vi /etc/login.defs # find the value PASS_MAX_DAYS and edit it to your needs
Now unmount the file system:
$ sudo umount /mnt/linuxrescue
Unactivate the LVM vol group:
$ sudo vgchange -an VolGroup00
Delete the partition mappings:
$ sudo kpartx -dv /dev/loop0
Unmount the loopback device:
$ sudo kpartx -dv /dev/loop0
KVM:Reset Windows Guest Password
by jfargen on Dec.21, 2012, under Work and stuff
The post is from the stand point of RHEL hypervisor with a KVM Windows guest using a raw image file as a backing store using the package chntpw, but it could easily be applied to different distros, backing stores, or even booting a Linux livecd as long as you can install the chntpw package. Some steps may vary depending on what kind of backing store you are using for the image and where your Windows OS was installed.
First get the chntpw package:
$ sudo yum install chntpw
Print the logical loopback device:
$ sudo losetup -f
/dev/loopo
Next mount the image file as a loopback device:
$ sudo losetup /dev/loopo /var/lib/libvirt/images/windows7.raw
Add partition mappings:
$ sudo kpartx -av /dev/loop0 #That is a zero at the end of /dev/loop0
Create a directory that can be used as a mount point:
$ sudo mkdir -p /mnt/winrescue
Mount the appropriate filesystem:
$ sudo mount /dev/mapper/loop0p2 /mnt/winrescue
Change to the directory where the SAM db is located:
$ sudo cd /mnt/winrescue/Windows/System32/config/
Now run the chntpw utility:
$ sudo chntpw -I SAM
Once complete you will want to unmount the filesystem and loopback device.
Get out of the mounted filesystem:
$ cd ~
Umount the filesystem:
$ sudo umount /mnt/windowsrescue/
Delete the partition mappings:
$ sudo kpartx -dv /dev/loop0
Unmount the loopback device:
$ sudo losetup -d /dev/loop0
The process is now complete.
VMWare / Linux: Map SCSI LUNs to sd (storage device id)
by jfargen on Oct.26, 2012, under Work and stuff
Hopefully one day you won’t come upon a server running ESX / Linux that has become unresponsive to regular management tools and view something like this completely filling your console:
sd 7:0:2:0 still retrying after 360s
I knew instantly 7:0:2:0 was a SCSI mapping for host, bus, scsi id, etc, etc. These hosts are using SATA drives and I needed to be able to us hdparm to determine the serial number of the drive for local support to replace. After digging I came up the command sg_map matched with -x option prints after each active sg device name is displayed there are five digits: <host_number> <bus> <scsi_id> <lun> <scsi_type>.
When I ran sg_map -x this provided me with exactly what I need: /dev/sg2 7 0 2 0 0 /dev/sdc. You can see that sdc is mapped to SCSI address 7:0:2:0. With this information I was able to use hdparm -i /dev/sdc to extract the serial number of the drive and provide it to local hands and feet support in Germany to swap out the failing hard drive.